Wireless Security with WPA2 (802.11i)
TLDR
- WEP is insecure
- WPA1 / WPA using TKIP is also insecure
- WPA2 is most secure (ensure KRACK is patched)
- 802.11i is complicated
Old Wireless Security WEP / WPA'1'
- WEP (Wired Equivalent Privacy)
- Old and Insecure [See Aircrack-NG] (https://www.aircrack-ng.org/)
- Stream Cipher RC4
- CRC-32 Checksum -WPA1 (AKA WPA using TKIP)
- Has similar attack vectors as WEP
**Note 802.11 Authentication: has 802.11 Management Frame called “Authentication” this is not related to any real authentication and is just part of wireless association… again not authentication, who names this stuff **
WPA / 802.11i
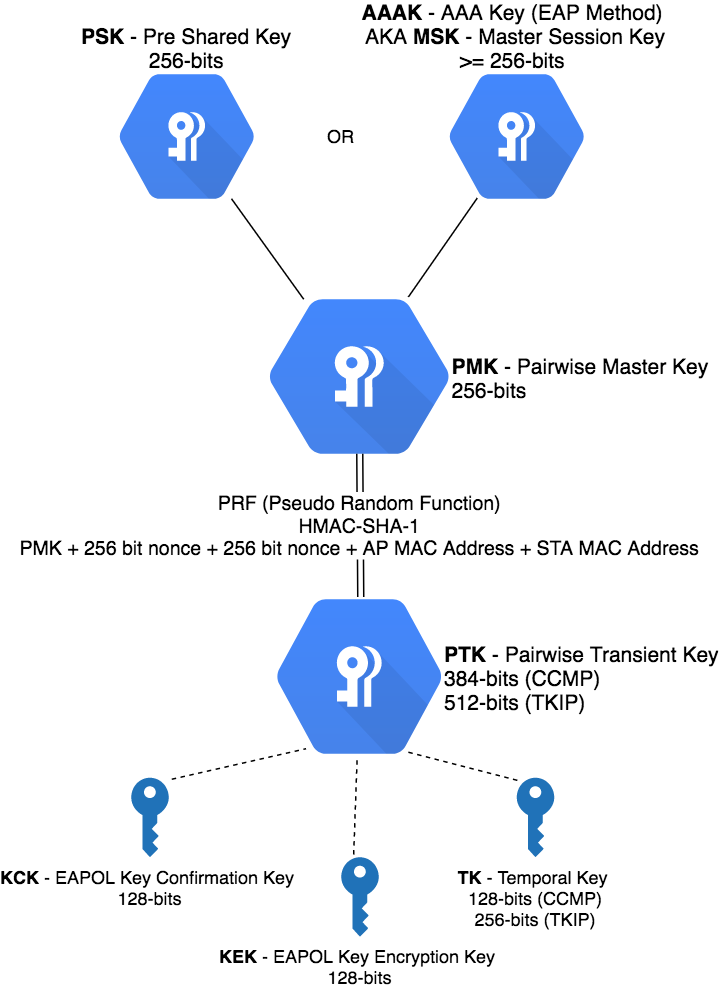
Defines what the standard refers to as Robust Security Network (RSN) which allows the creation Robust Security Network Association (RSNA) which is a logical connection between entities through a key management scheme. Keys are “shared” (really just validated) through the “4-Way Handshake” which validates a Pairwise Master Key (PMK), which is used to create and install temporal keys, which are what are used to encrypt your wireless data.
- PMK is generated 2 ways
- Pre Shared Key (PSK) WPA2[-PSK]
- Distruibuted through EAP (802.11x) WPA2-Enterprise
Key Hierarchy
- Shared Key: this could be a pre-shared key (PSK), or 802.1x with EAP Method (PEAP, TLS, etc.)
- The shared key generates a PMK (Pairwise Master Key)
- Through HMAC the PMK generates a PTK (Pairwise Temporal Key)
- The PTK consists of 3 different Keys
- EAPOL-KCK: Used to support integrity and data origin authenticity of STA-to-AP Control Frames, Proof of Possession of PMK
- EAPOL-KEK: Protects confidentiality of Keys and other data during RSNA
- TK: Used for the actual protection of user traffic
802.11i Key Table
| Name | Description |
|---|---|
| AAA Key | Used to derive PMK. Uses 802.1x for authentication. AKA MSK |
| PSK (Pre Shared Key) | Used as the PMK, where PSK is used as Authentication |
| PMK (Pairwise Master Key) | Derived from PSK or AAA Keys, used to derive PTK |
| GMK (Group Master Key) | Used to derive the GTK |
| PTK (Pairwise Transient Key) | Derived from the PMK, Contains KCK, KEK, and TK keys |
| TK (Temporal Key) | Part of the PTK, Used with TKIP, CCMP, GCMP to provide encryption (confidentiality and integrity) for unicast traffic |
| GTK (Group Temporal Key) | Derived from GMK, Used to provide encryption to Multicast and broadcast traffic |
| MIC-Key (Message Integrity Code Key) | Used by TKIP Michael MIC to provide integrity of messages |
| EAPOL-KCK (EAPOL-Key Confirmation Key) | Part of PTK, used to provide integrity of keying material during 4-way handshake |
| EAPOL-KEK (EAPOL-Key Encryption Key) | Part of PTK, used to ensure confidentiality of the GTK and TK during the 4-way handshake |
| WEP Key (Wired Equivalent Privacy Key) | PSK used with WEP |
TKIP
- Was only inlace to improve security from WEP while providing backward compatibility to AP and Devices
- Crypto:
- RC4 for Confidentiality
- Michael for Integrity/ MIC
- MIC is subject to cryptanalysis attack
- Implementation
- 3 Keys (2 Integrity 1 Encryption)
- There is 1 MIC for each channel between the AP and Device (Up and Down) remember WiFi is Half Duplex
- There are TKIP Sequence Counters (TSC) assigned to each frame preventing replay attacks (if frames are not received in order they are dropped)
- Each frame is encrypted with a new key, generated from the TK and TSC
- Attack Countermeasures
- Logging MIC failures as they indicate attack
- Limiting MIC failures (2 MIC failures in 60-seconds terminates the connection)
- Changing the PTK and GTK periodically
CCMP
- Was design without the hardware and crypto restrictions like TKIP
- CCMP is based on CCM (block cipher mode of AES)
- CCM uses CTR for Confidentiality and (CBC-MAC) for authentication and integrity
- CCM for 802.11 uses a 128-bit session key (this is the TK) for each duplex channel
- CCMP has a keyspace of 2^128, and 48-bit packet number (PN) used as a nonce (preventing replay attacks)
- Implementation
- PN (Packet Number) is maintained for the session is incremented
- The PN (with QoS priority) + Transmit-address generated the nonce
- The TK (or Key ID) and PN are combined forming the CCMP header
- Additional Authentication Data (AAD) includes the QoS field and several mac addresses
- The TK + PN + AAD + Packet Data are combined to create the ciphertext payload
- The frame will look like [MAC Header][CCM Header][Cipher Text + MIC]
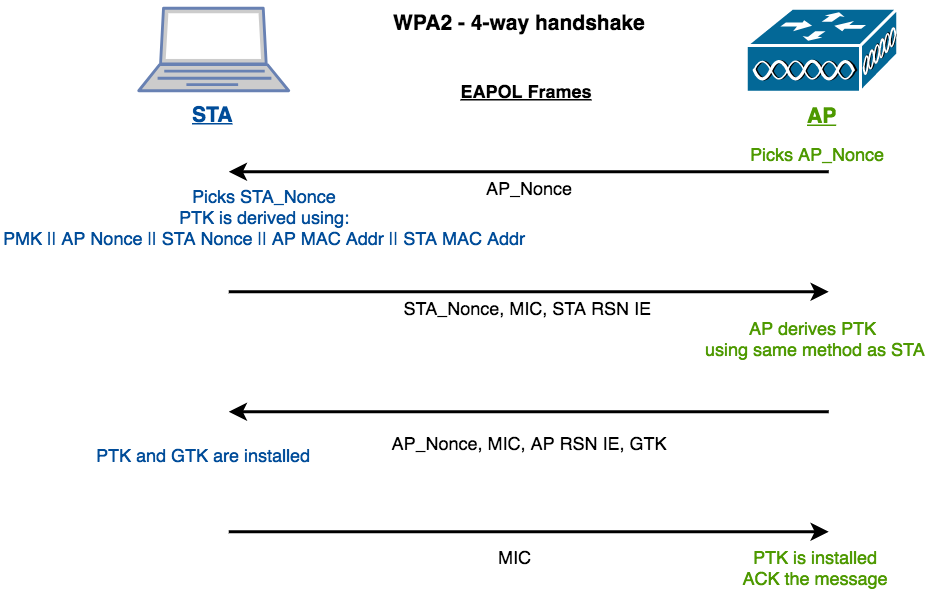
802.11i 4Way-HandShake
-
4 Frames are used in the handshake to generate the PTK and ensure mutual authentication of the MSK or (same shared key)
-
- AP sends AP_Nonce and MAC address
- STA derives PTK using (PMK || AP Nonce || STA Nonce || AP MAC Addr || STA MAC Addr)
- 2: STA send STA_Nonce, MIC, and STA RSN IE
- AP derives PTK using the same as above
- 3: AP sends AP_Nonce, MIC, and AP RSN IE, GTK
- STA installs PTK and GTK
- 4: STA sends MIC
- This an ACK of the last message
-
-
RSN IE (Information Elements) shared they type of crypto, and keys used
References
NIST - Guide to IEEE 802.11i IEEE 802.11i Summary CWNP 802.11i Keys